- Filter by
- Categories
- Tags
- Authors
- Show all
- All
- Apple
- Blog
- Business
- Cybersecurity
- Dell
- Gaming
- GEEX
- HP
- Laptops
- Leasing
- Lenovo
- Macbook Pro
- Microsoft
- Microsoft Surface Family
- Monitors
- News
- Printing
- Technology
- Uncategorized
- Windows
- All
- #CorporateResponsibility
- #DigitalFuture
- #DigitalTransformation
- #EcoFriendly
- #Ewaste
- #FutureOfWork
- #Innovation
- #RecycleElectronics
- #ReduceEwaste
- #Sustainability
- #SustainableBusiness
- #TechInnovation
- #TechLeadership
- #TechTrends
- #WorkplaceTransformation
- 16GB RAM
- 2023 Annual Cybersecurity Attitudes and Behaviours Report
- 32GB RAM
- 365
- 365 Copilot
- 4070
- 4080
- 4090
- 4GB RAM
- 4K
- 5 stars
- 5-stars
- 64GB RAM
- 8GB RAM
- Activity Monitoring
- Ad Blockers
- Adobe Photoshop
- Advanced Threats
- adware
- Ai
- AI Data Breaches
- AI Laptop
- AI Laptops
- AI Rules
- AI tools
- AI-Enabled PCs
- Air Pod
- Air Pod MAX
- Air Pod Pro
- Air Pods
- alienware
- alienware computer
- alienware computer laptops
- alienware computer lease
- alienware computer leasing
- alienware computer renting
- Alienware computers
- alienware gaming
- alienware gaming laptop
- alienware gaming laptops
- Alienware Laptop
- alienware laptop lease
- alienware laptop pay monthly
- alienware laptop pay weekly
- alienware laptop rental
- Alienware Laptops
- alienware laptops on finance
- alienware lease
- alienware rental
- alineware computer rental
- Amazon
- Amazon Voucher
- Amazon Vouchers
- AMD
- AMD Radeon
- AMD Ryzen
- AMD Ryzen 5
- AMD Ryzen 7
- AMD Ryzen 9
- AMD Ryzen vs Intel Core
- and Conformance
- Anti-Malware
- Anti-Malware Software
- Anti-phishing
- Anti-phishing Software
- Antivirus
- Antivirus software
- App Permissions
- Apple
- Apple AI
- Apple Air Pods
- Apple Airpods 2nd generation
- Apple Event
- Apple Glow Time
- Apple Glowtime
- Apple iMac
- Apple iMac Lease
- Apple iMac M3
- Apple iMac M3 Series
- Apple iMac Series
- Apple iMacs
- Apple Intelligence
- Apple Intelligence AI
- Apple iPad Leasing
- apple ipad pro
- Apple iPad Rental
- Apple iPhone
- Apple iPhone 16
- Apple iPhone 16 Pro
- Apple iPhone 16 Pro MAX
- Apple It's glowtime
- Apple Laptops
- Apple Lease
- Apple Leasing
- Apple M3 Chip
- Apple M3 Chip Series
- Apple Mac
- Apple Mac Mini
- Apple Mac Mini Finance
- Apple Mac Mini Lease
- Apple Mac Mini Pay Monthly
- Apple Mac Mini Pay Weekly
- Apple Mac Mini Rental
- Apple Mac Pro
- Apple Mac Pro Lease
- Apple Mac Pro Leasing
- Apple Mac Studio
- Apple Mac Studio Leasing
- Apple Mac Studio Rental
- Apple MacBook
- Apple MacBook Air
- Apple MacBook Pro
- Apple MacBook Pro 14" M3
- Apple MacBook Pro 16" M3
- Apple MacBook Pro M3
- Apple MacBook Pro M4
- Apple Mini Mac
- Apple News
- Apple Pencil
- Apple Rental
- Apple Renting
- apple TV
- Apple Vision Pro
- apple watch
- Apple watch series 10
- Architects
- Artificial Intelligence
- artificial intelligence laptop
- artificial intelligence laptops
- ASUS
- ASUS Gaming
- ASUS Gaming Laptop
- ASUS Gaming Laptop ROG Strix
- ASUS Gaming Laptop ROG Zephyrus
- ASUS Gaming Laptop TUF
- ASUS Gaming Laptops
- ASUS Laptop
- ASUS Laptops
- ASUS ROG
- ASUS ROG STRIX
- ASUS ROG STRIX gaming laptop
- ASUS ROG TUF
- ASUS ROG TUF gaming laptop
- Asus ROG Zephyrus
- ASUS TUF
- Audit Trails
- Auto-Fill
- Automated Response
- Automation
- Background App Refresh
- Battery Drain
- Battery Health
- Battery LIfe
- BEC
- Benefits of Leasing
- best laptops for multitasking and performance
- best laptops for online meetings and collaboration
- best laptops for portability and battery life
- best laptops for productivity and comfort
- best laptops for remote work
- best laptops for video editing and streaming
- best laptops for working from home 2023
- Bing Chat
- Birmingham
- Birmingham Computer Leasing
- Birmingham Laptop Leasing
- BMind Smart Mirror
- Browser Extension
- Browser Extensions
- budget
- business
- Business Email Compromise
- Business Laptop
- Business Laptop Lease
- Business Laptop Leasing
- Business Laptop Rental
- Business Laptops
- Business Password Management App
- Business RAM
- Cash Flow
- Centralised Password Management
- Chatbots
- cheap core i5 desktops
- cheap core i5 laptops
- cheap i5 desktop
- cheap i5 laptops
- Cleaning Your Laptop
- Cleaning Your Laptop Screen
- Clear Communication
- Clipchamp Video Editor
- Cloud
- Cloud Adoption
- Cloud Audit
- Cloud Backups
- Cloud Computing
- Cloud Solution
- Cloud Solutions
- Cloud Storage
- Cloud Waste
- Cloud-Based Collaboration
- CLOUD-BASED EMAIL
- Cloud-Based Services
- Cloud-Centric Security
- Company Culture
- Company Laptop
- Company Laptops
- Compliance
- computer
- computer lease
- Computer Leasing
- computer leasing companies
- computer leasing company
- computer leasing pay monthly
- computer leasing pay weekly
- computer rental
- computer rental birmingham
- Computer renting
- Computer Security
- computers
- Conditional Access
- Connectivity
- Continuous Monitoring
- Continuous Verification
- Copilot
- Copilot+Pc
- core i5
- Core i5 desktop
- core i5 desktop pay monthly
- core i5 desktop pay weekly
- core i5 desktops
- core i5 gaming desktop
- core i5 gaming laptop
- Core i5 laptop
- core i5 laptop leasing
- core i5 laptop pay monthly
- core i5 laptop pay weekly
- core i5 laptop rental
- core i5 laptops
- core i5 or core i7
- core i5 processor
- Core i5 Processors
- core i5 surface pro
- core i5 tablet
- core i7
- Core i7 computer
- core i7 computers
- Core i7 Laptops
- Core i7 processor
- core i7 processors
- core i9
- core i9 computer
- core i9 computers
- core i9 Laptop
- core i9 Laptops
- core i9 processor
- core i9 processors
- Core Ultra
- Core Ultra 5
- Core Ultra 7
- Core Ultra 9
- cost savings
- CPU
- Cyber
- cyber hygiene
- Cyber Insurance
- Cyber Threats
- cyberattack
- cyberattacks
- Cybercrime
- Cybercriminals
- Cybersecurity
- Cybersecurity Assessment
- Cybersecurity Attitudes
- Cybersecurity Attitudes and Behaviours Report
- Cybersecurity Audit
- Cybersecurity Audits
- Cybersecurity Awareness
- Cybersecurity Awareness Training
- Cybersecurity Measures
- Cybersecurity Risk
- Cybersecurity services
- Cybersecurity Training
- DALL.E 3
- Data
- Data Accuracy
- Data Analytics
- Data Breach
- Data Breaches
- Data Governance
- Data Loss Prevention
- data management
- Data Migration
- Data Protection
- data security
- Data Security Assessment
- Data Visualization
- Data-Driven Decision Making
- Deepfake
- Deepfakes
- Dell
- Dell Alienware
- Dell Alienware Laptop
- Dell Alienware Laptops
- Dell Finance
- Dell Financing
- Dell Laptop Leasing
- Dell Laptop Rental
- Dell Laptops
- Dell Latitude
- Dell Latitude 7350
- Dell Lattitude
- Dell Lease
- Dell Leasing
- Dell Rental
- Dell Rentals
- Dell XPS
- DELL XPS 13
- DELL XPS 14
- Designers
- desktop leasing
- desktop rental
- Device Security
- Devices and Network Infrastructure
- Digital Clutter
- DKIM
- DLP
- DMARC
- DMARC Policy
- DNS
- Domain Keys
- Domain-based Message Authentication
- DomainKeys Identified Mail
- E-COMMERCE
- Efficiency
- Email Assistants
- Email Authentication
- Email Security
- Emergency IT Support
- Employee Phishing Awareness
- Employee Phishing Awareness Training
- Employee Satisfaction
- Employee Wellbeing
- Encrypted Messaging
- Encrypted Storage
- End-to-End Encryption
- ENTERPRISE RESOURCE PLANNING
- environment
- Environmental Responsibility
- ERP
- Evie Ring
- Evolving Technologies
- Excel
- Face-Swapping Deepfakes
- Feedback
- Feefo
- Feefo Review
- FHD
- finance ipad
- Firewalls
- Firmware
- flexibility
- Gamer
- Gaming
- Gaming Console
- gaming desktop
- gaming desktop for business
- gaming desktop pay monthly
- gaming desktop pay weekly
- gaming desktop rental
- Gaming desktops
- Gaming equipment
- Gaming Laptop
- gaming laptop finance
- gaming laptop for business
- Gaming Laptop Lease
- gaming laptop pay monthly
- Gaming Laptop pay weekly
- Gaming Laptop Rental
- Gaming Laptops
- gaming laptops lease
- gaming laptops leasing
- Gaming laptops rental
- gaming pc
- gaming pc lease
- gaming pc rental
- GEEX
- GEEX Leasing
- GEEX rental
- GeForce RTX
- GoDaddy
- Google Review
- Graphic Design
- Graphic Designer
- Graphic Designers
- Graphics
- graphics card
- Hacktivism
- hardware
- hidden malware
- Hire a Laptop
- Hire a Laptop Instead of Purchasing
- home office computers
- home office laptops
- How much RAM do I need
- how to clean a laptop
- how to clean a laptop safely
- How to Use a Laptop as a Monitor
- How to Use a Laptop with a Gaming Console
- HP
- HP EliteBook
- HP Gaming
- HP Gaming Desktops
- HP Gaming Laptops
- HP leasing
- HP Omen
- HP Omen Desktop
- HP Omen Laptop
- HP ProBook
- HP rental
- HTTPS
- Hybrid Work
- Hybrid Working
- i3
- i5
- i5 or i7
- i5 vs i7
- i7
- i7 Laptop
- i7 Laptops
- i9
- i9 Laptop
- i9 laptop lease
- i9 laptop leasing
- i9 laptop pay monthly
- i9 laptop pay weekly
- i9 laptop rent
- i9 laptop rental
- i9 Laptops
- iMac
- iMac Business Lease
- iMac Leasing
- iMac M3
- iMac M3 Series
- iMac Monthly Payments
- Incident Response
- Intel
- intel core
- Intel Core i5
- intel core i5 desktop
- Intel core i5 desktops
- intel core i5 laptop
- Intel core i5 laptops
- Intel Core i7
- intel core i7 computer
- intel core i7 computers
- intel core i7 laptop
- intel core i7 laptops
- Intel Core i7 Processor
- Intel Core i7 Processors
- intel core i9
- Intel core processor
- Intel processors
- Internet of Things
- iOS
- iOS 18
- IoT
- IP
- iPad
- iPad (10th Gen)
- iPad Air M1
- ipad deals
- ipad finance
- ipad financing
- iPad Mini
- iPad Mini (6th Gen)
- ipad monthly
- ipad monthly payments
- ipad on finance
- ipad on pay monthly
- ipad pay monthly
- iPad Pro
- iPad Pro (M4
- ipad pro finance
- ipad weekly
- iPadOS 18
- ipads on finance
- ipads pay weekly
- iPhone
- iPhone 15 Pro
- iPhone Running Slow
- iPhones
- IPSec
- IT
- IT leasing
- IT Leasing Birmingham
- IT rental
- IT rental Birmingham
- IT security
- IT Service
- IT Services
- IT solutions
- IT Support
- IT Support Birmingham
- IT Support Service
- Keyboard
- laptop
- laptop battery
- laptop comparison
- Laptop Computer
- Laptop Computer lease
- Laptop Computer Leasing
- Laptop Computer Rent
- Laptop Computer Rental
- Laptop for Architect
- Laptop for Architects
- laptop hire
- laptop insurance
- laptop lease
- Laptop Lease Birmingham
- Laptop Leasing
- laptop leasing benefits
- Laptop Leasing in the UK
- Laptop Leasing UK
- laptop lifespan
- laptop maintenance
- laptop models
- laptop OS
- laptop performance
- laptop processors
- laptop rental
- Laptop Rental Birmingham
- Laptop Rental in Birmingham
- laptop rentals
- laptop renting
- laptop reviews
- laptop tips
- laptop upgrade
- Laptops
- Laptops Birmingham
- Laptops for Architect
- Laptops for Architects
- Laptops for lease Birmingham
- Laptops for rent Birmingham
- laptops for working from home
- laptops renting
- Latest Tech
- Latitude
- LEASE
- Lease a ASUS Gaming Laptop
- Lease a ASUS Laptop
- Lease a Dell Laptop
- lease a gaming laptop
- lease a ipad
- lease a laptop
- lease a laptop Birmingham
- Lease a Laptop Computer
- Lease a Lenovo Laptop
- Lease a MacBook Air
- Lease a monitor
- Lease a Printer
- Lease a Surface Pro
- lease an alienware laptop
- lease an apple ipad
- lease an ipad
- Lease iMac for Business
- leasing
- Leasing a Laptop Computer
- Leasing a laptop in Birmingham
- Leasing a MacBook Air
- leasing a monitor
- Leasing computers
- Leasing iMac
- leasing laptop
- Leasing Laptops UK
- Leasing Tech
- Lenovo
- Lenovo Company Laptop
- Lenovo Company Laptops
- Lenovo Computer
- Lenovo Gaming Laptop
- Lenovo Laptop
- Lenovo Laptop Leasing
- lenovo laptop on finance
- Lenovo Laptop Rental
- Lenovo Laptops
- Lenovo lease
- Lenovo Leasing
- Lenovo Legion
- LENOVO Legion Pro 5i Gen 8
- Lenovo Rental
- Lenovo ThinkPad
- Lenovo ThinkPad Leasing
- Lenovo ThinkPad X1
- Lenovo ThinkPad X1 Carbon Gen 12
- Lenovo ThinkPads
- LG 4K Transparent OLED TV
- LIPCURE BEAM
- Log Management
- M3
- M3 Chip
- M3 Chip Series
- M3 MacBook
- M3 Max
- M3 PRO
- M365
- M365 apps
- M4
- M4 Chip Series
- M4 Max
- M4 Max chip
- M4 Pro
- Mac
- Mac Lease
- Mac Leasing
- Mac Mini
- Mac Mini Leasing
- Mac Pro
- Mac Pro Rack
- Mac Pro Rack M2
- Mac Pro Rack M2 Ultra
- Mac Pro Tower
- Mac Pro Tower M2
- Mac Pro Tower M2 Ultra
- Mac Rental
- Mac Studio
- Mac Studio Lease
- Mac Studio Leasing
- Mac Studio Rental
- Mac Studio Renting
- MacBook
- MacBook Air
- MacBook Air 13-inch
- MacBook Air 15
- MacBook Air 15 Lease
- MacBook Air 15-inch
- MacBook Air 15"
- MacBook Air 15" Lease
- MacBook Air 15" Leasing
- MacBook Air Lease
- MacBook Air leasing
- MacBook Air M1
- MacBook Finance
- MacBook Lease
- MacBook M3 Chip
- MacBook Pro 14
- MacBook Pro 14-inch
- MacBook Pro 14" M3
- MacBook Pro 16
- MacBook Pro 16-inch
- MacBook Pro 16" M3
- MacBook Pro M3
- MacBook Rental
- macOS
- Magic Keyboard
- Maintenance
- Malware
- Malware Traps
- master password
- Master Search
- Memory
- MFA
- Microsoft
- Microsoft 365
- Microsoft 365 Business
- Microsoft 365 Copilot
- Microsoft Computer Surface Pro
- Microsoft Computers Surface
- Microsoft Computers Surface Pro
- Microsoft Copilot
- Microsoft Defender
- Microsoft Defender External Attack Surface Management
- Microsoft Defender for Cloud
- Microsoft Defender SmartScreen
- Microsoft Defender Threat Intelligence
- Microsoft Defender XDR
- Microsoft Edge
- Microsoft Edge Browser
- Microsoft Edge Features
- Microsoft Edge Workspaces
- Microsoft Entra
- Microsoft Intune
- Microsoft Laptops
- Microsoft Leasing
- Microsoft Planner
- Microsoft Purview
- Microsoft security
- Microsoft Security Copilot
- Microsoft Sentinel
- Microsoft Shopping
- Microsoft Surface
- Microsoft Surface Computer
- Microsoft Surface Computer models
- Microsoft Surface Laptop
- Microsoft Surface Laptop Lease
- Microsoft Surface Laptop Rental
- Microsoft Surface Laptop Studio 2
- Microsoft Surface Laptops
- Microsoft Surface Lease
- Microsoft Surface Leasing
- Microsoft Surface Pro
- Microsoft Surface Pro 9
- Microsoft Surface Pro 9 Leasing
- Microsoft Surface Pro 9 Rental
- Microsoft Surface Pro Computer
- Microsoft Surface Pro Computer Lease
- Microsoft Surface Pro Computer Leasing
- Microsoft Surface Pro Lease
- Microsoft Surface Pro Leasing
- Microsoft Surface Pro Rent
- Microsoft Surface Pro Rental
- Microsoft Teams
- Mini LED TVs
- Mini Mac Computer
- Mini Mac Computers
- Mini Mac Computers Lease
- Mini Mac Computers Leasing
- Mini Mac Computers Pay Monthly
- Mini Mac Computers Rental
- Mini Mac Computers Renting
- Mobile Computers
- Mobile Computing
- Mobile Device Security
- Mobile Malware Traps
- Mobile Security
- Mobile-Friendly
- monitor
- Monitor Lease
- Monitor Leasing
- monitor pay monthly
- monitor pay weekly
- Monitor Rent
- Monitor Rental
- monitors
- monitors on finance
- MS Teams
- MSI
- MSI Gaming
- MSI Gaming Laptop
- MSI Katana
- MSI Laptop
- MSI Laptops
- Multi-Factor Authentication
- Mymanu CLIK Pro Immersive Translation Earbuds
- NAC
- Network Access Control
- Network Infrastructure
- Network Issues
- Network Traffic Analysis
- New Apple Chip M3
- New iMac 24" M3
- New iMac M3
- New MacBook Pro 14" M3
- New MacBook Pro 16" M3
- New MacBook Pro M3
- New technology
- NPUs
- NVIDIA GeForce
- NVIDIA GeForce RTX
- NVIDIA GeForce RTX 4070
- NVIDIA GeForce RTX 4080
- NVIDIA GeForce RTX 4090
- office computers
- office laptops
- Office Productivity
- Online Gaming Services
- online safety
- Online Security
- OpenVPN
- Operating system
- ORo Dog Companion
- Outlook
- Password
- Password Generation and Complexity
- Password Manager
- Password Managers
- Password Sharing
- passwords
- pay for ipad monthly
- pay monthly for ipad
- Pay Monthly iPad
- Pay Monthly iPad Deal
- Pay Monthly iPad Deals
- Pay Monthly iPads
- pay monthly lenovo laptop
- pay weekly for ipad
- pay weekly ipad
- Pay Weekly iPad Deals
- pay weekly ipads
- pay weekly lenovo laptop
- PayPal
- performance
- Phishing
- Phishing Attacks
- Phising
- Phone Password Managers
- portable laptops
- PowerPoint
- PPTP
- Precision
- Printer
- Printer Leasing
- Printer Monthly payments
- Printer Rental
- Printer Weekly Payments
- Printers
- Printers Leasing
- Printers Rental
- Pro 9 Surface
- Processor
- processors
- productivity
- Project Management
- Project Management Tools
- Protocols
- PS5
- QR
- QR Code
- QR Codes
- Qualcomm
- Qualcomm Snapdragon
- RaaS
- RAM
- Ransom Attacks
- Ransomware
- Ransomware-as-a-Service
- razer blade
- Razer Blade Gaming
- Razer Blade Gaming Laptop
- Razer Blade Laptops
- Razer Blade Lease
- Razer Blade Leasing
- Razer Blade Rental
- Razer Blade Renting
- REMOTE COLLABORATION
- Remote Work
- Remote Work Options
- rent a apple ipad
- Rent a ASUS Gaming Laptop
- rent a computer
- Rent a Dell Laptop
- Rent a gaming laptop
- rent a laptop
- Rent a laptop Birmingham
- Rent a Laptop Computer
- rent a laptop uk
- Rent a Lenovo Laptop
- Rent a MacBook Air 15"
- Rent a Printer
- Rent a Surface Pro
- rent an alienware laptop
- rent an apple ipad
- Rent an ASUS Gaming Laptop
- rent an i5 laptop
- rent an ipad pro
- rent apple ipad
- rent to own apple ipad
- Rent to Own iPad
- rental
- Rental iPad
- rental laptop
- Rental Laptops
- rented laptop
- Renting a Laptop Computer
- Renting a laptop in Birmingham
- renting laptop
- Replace Your Business Laptop
- Replace Your Business Laptops
- Response Plan
- Restart
- review
- Reviews
- ROG
- ROG Strix
- ROG Zephyrus
- Ryzen
- Ryzen 3
- Ryzen 7
- Ryzen 9
- Ryzen vs Intel
- Samsung S95D OLED TV
- Samsung Self-Driving-based Home Buddy
- Scam
- Scanning QR Codes
- schools
- secure global network
- Secure Password Sharing Features
- Secure Storage
- security
- Security Copilot
- Security Information and Event Management
- Security Posture
- Security software
- security updates
- Sender Policy Framework
- SGN
- Shadow IT
- SIEM
- small and medium-sized businesses
- small business
- Small Business UK
- Small Businesses
- Smart Calendars
- Smart Home
- smart home device
- smart home devices
- Smart Home Tech
- Smart Homes
- smart house
- Smart Office
- smart phone
- Smart Space
- smart tech
- SMBs
- smishing
- Snap Layouts
- Snapdragon
- Snapdragon Laptops
- Snapdragon Processors
- Social Engineering
- software
- Solutions
- Spear Phishing
- SPF
- SSH
- SSL
- SSTP
- Stolen Credentials
- Storage
- Strengthen Your Passwords
- Stripe
- Support
- Surface Laptop
- Surface Laptop Lease
- Surface Laptop Leasing
- Surface Laptop Rental
- Surface Laptop Studio 2
- Surface laptops
- Surface Leasing
- Surface Microsoft Pro
- Surface Microsoft Pro series
- Surface Pro
- Surface Pro 8 LTE
- Surface Pro 9
- Surface Pro Computer
- Surface Pro Computer Finance
- Surface Pro Computer Lease
- Surface Pro Computer Leasing
- Surface Pro Computer Monthly Payment
- Surface Pro Computer Rent
- Surface Pro Computer Rental
- Surface Pro Computer Weekly Payment
- Surface Pro Lease
- Surface Pro Leasing
- Surface Pro Rent
- Surface Pro Rental
- Surface Pro X
- Switch
- Task Managers
- Tax
- tax benefits
- tax deductible
- Teams
- Teams Payment
- Tech
- tech training
- Tech Upgrades
- technology
- Technology Modernisation
- Technology Training
- ThinkPad
- ThinkPad Leasing
- ThinkPad P Series
- ThinkPad Rental
- ThinkPad T Series
- ThinkPad X1 Carbon
- Threat Detection
- Threat Identification
- Threat identification & response
- Threat Modeling
- Threat Modelling
- Tips For 2025
- top laptops for home office
- touch screen
- Touch Screen Laptop
- Touch Screen Laptops
- touch screen technology
- Touch screens
- Touchpad
- two-factor authentication
- UHD
- UK
- Unified Communication
- Unified Communication Platforms
- Upgrade Your Laptop
- Upgrade Your Laptops
- Use a Laptop as a Streaming Device
- Use a Laptop with a Gaming Console
- Used Laptop
- User Activity Monitoring
- User Experience
- Verification Process
- VIDEO CONFERENCING
- Virtual Assistants
- Virtual Meeting Helpers
- Virtual Private Network
- Virtual Private Networks
- Vision Pro
- visionOS
- Vouchers
- VPN
- VPNs
- Vulnerability Assessment
- Vulnerability Scanning
- what is RAM
- Which iPad is Best
- Wi-Fi Encryption
- Windows
- Windows 10
- Windows 11
- Windows Laptops
- Word
- Work-Life Balance
- Workflow
- Workforce Technology
- Workforce Technology Modernisation
- working from home laptops
- working from home office laptops
- WWDC
- WWDC24
- Xbox Series X
- Xero
- XPS
- Yahoo
- Zephyrus G14
- Zero Trust
- Zero Trust Security
24 June 2024
24 June 2024
Patching holes after a breach is too late! Continuous monitoring helps identify vulnerabilities before attackers exploit them. Read our latest article to learn why it's essential for cybersecurity.
Do you like it?
21 June 2024
21 June 2024
Unlock your team's full potential! Don't let tech illiteracy hinder your business. Our latest article discusses the hidden costs and offers tips to bridge the tech gap.
Do you like it?
28 May 2024
28 May 2024
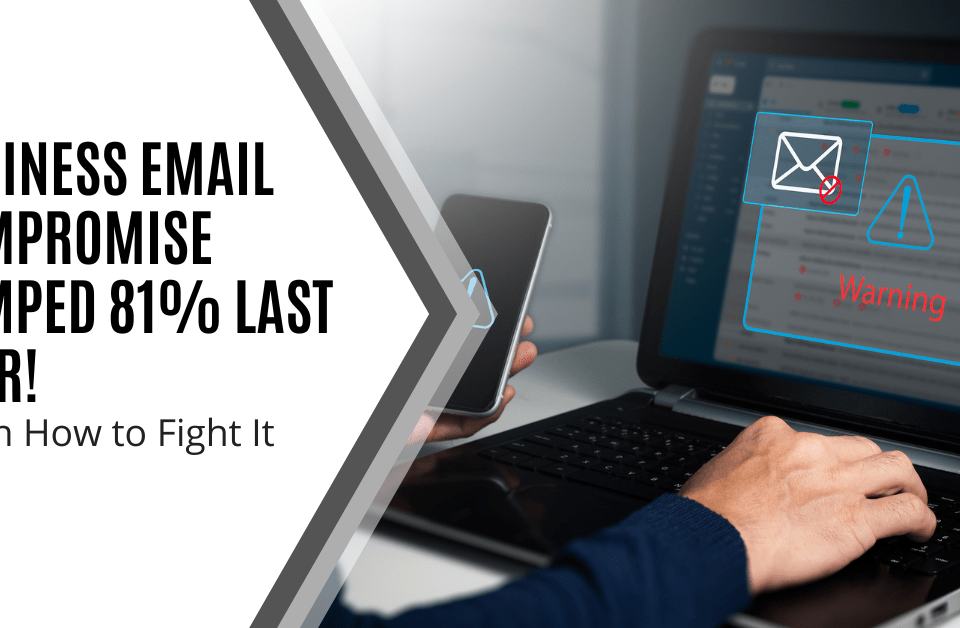
Does your team know how to spot a phishing email from a compromised company account? Find out why BEC attacks are so dangerous and how to fight them.
Do you like it?
13 May 2024
13 May 2024
Drowning in data? Our guide helps you take control! Learn the key steps to improve your company's data management & unlock valuable insights.
Do you like it?